Industrial Machines like Cranes, Excavators Can Easily be Hacked with Software Defined Radios
Recently, the RF research team at Trend Micro released a very nice illustrated report, technical paper and several videos demonstrating how they were able to take control of building cranes, excavators, scrapers and other large industrial machines with a simple bladeRF software defined radio. Trend Micro is a well known security company mostly known for their computer antivirus products.
Trend write that the main problem stems from the fact that these large industrial machines tend to rely on proprietary RF protocols, instead of utilizing modern standard secure protocols. It turns out that many of the proprietary RF commands used to control these machines have little to no security in place.
A Forbes article written about the research writes:
Five different kinds of attack were tested. They included: a replay attack, command injection, e-stop abuse, malicious re-pairing and malicious reprogramming. The replay attack sees the attackers simply record commands and send them again when they want. Command injection sees the hacker intercept and modify a command. E-stop abuse brings about an emergency stop, while malicious re-pairing sees a cloned controller take over the functions of the legitimate one. And malicious reprogramming places a permanent vulnerability at the heart of the controller so it can always be manipulated.
So straightforward were the first four types of attack, they could be carried out within minutes on a construction site and with minimal cost. The hackers only required PCs, the (free) code and RF equipment costing anywhere between $100 and $500. To deal with some of the idiosyncracies of the building site tech, they developed their own bespoke hardware and software to streamline the attacks, called RFQuack.
Being a responsible security firm, Trend Micro has already notified manufacturers of these vulnerabilities, and government level advisories (1, 2) and patches have already been rolled out over the last year. However the Forbes article states that some vulnerabilities still remain unpatched to this day. Of interest, the Forbes articles writes that for some of these vendors the simple idea of patching their system was completely new to them, with the firmware version for some controllers still reading 0.00A.
The videos showing the team taking control of a model crane, real crane and excavator are shown below. The video shows them using bladeRF 2.0 SDRs which are relatively low cost TX/RX capable software defined radios. We also recommend taking a look at Trends web article as it very nicely illustrates several different RF attack vectors which could apply to a number of different RF devices.
In the past we've also posted about similar serious RF attacks to infrastructure and machines that reveal the vulnerability and disregard to wireless security present in everyday systems. These include vulnerabilities like taking control of city disaster warning sirens, GPS spoofing of car navigation systems, hacking wireless door systems on cars, and revealing hospital pager privacy breaches.
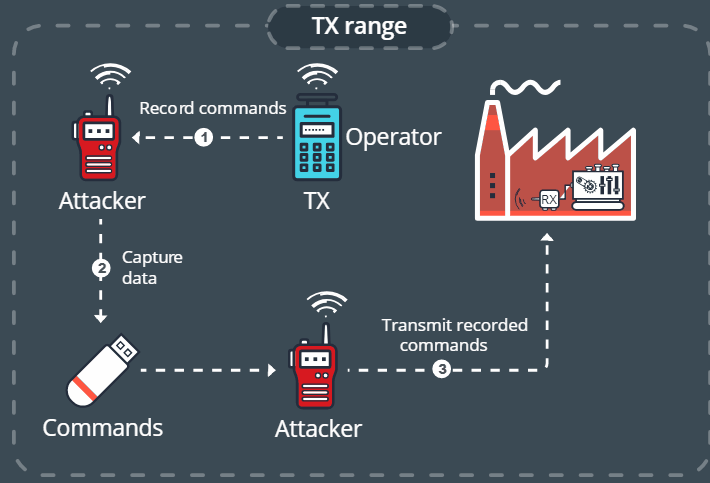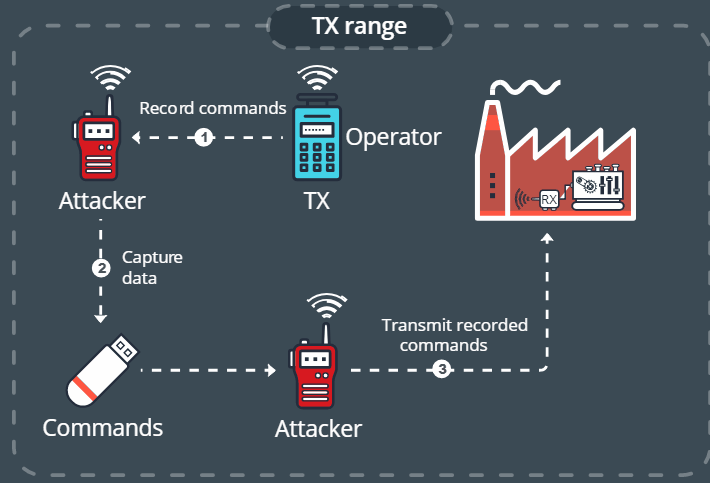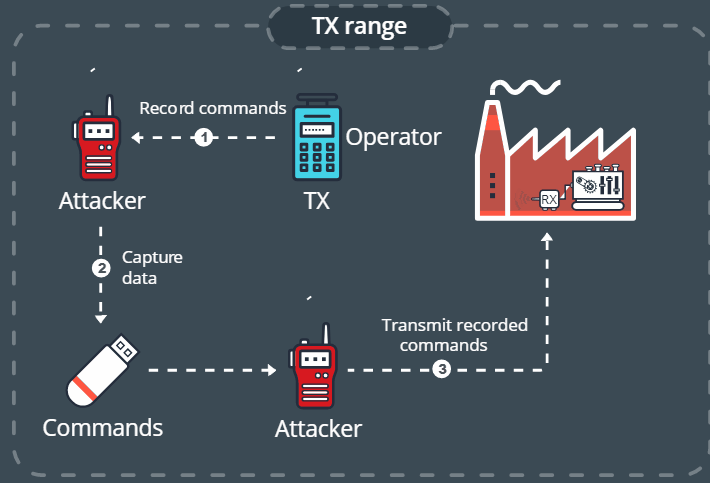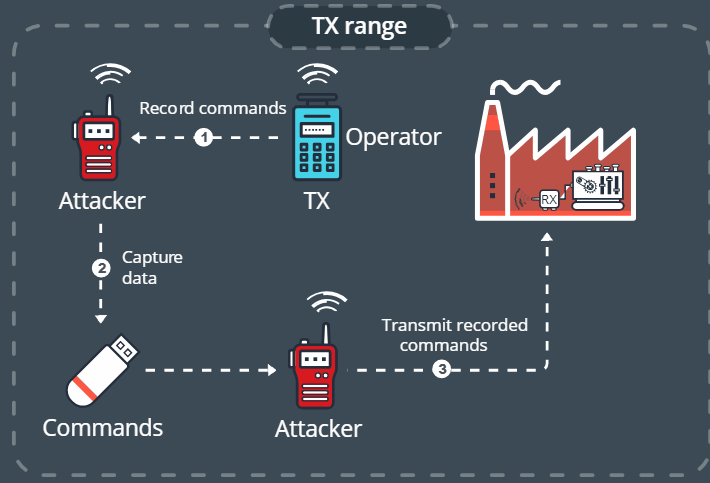
Great, so now we’re going to possibly have some Muhameed Iwilljabu remotely drving a cat D12 through a gay bar……with Allyuha Ackbar written all over it…..what hath thy world cometh too.
Or real life super sized battle bots!
Or some Islamophobes driving a crane through a mosque. What indeed.