Using a HackRF to Spoof GPS Navigation in Cars and Divert Drivers
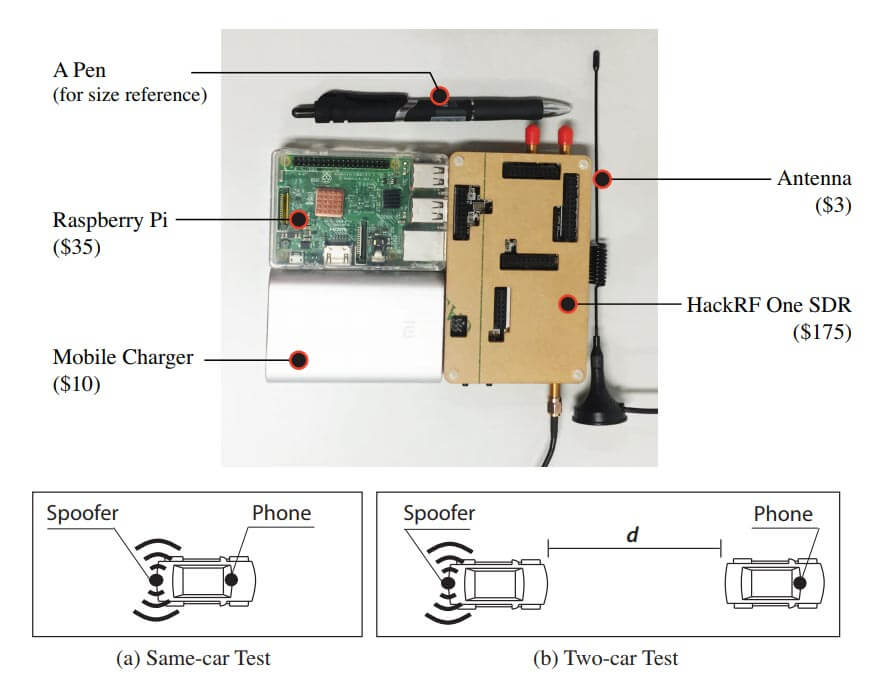
Researchers at Virginia Tech, the University of Electronic Science and Technology of China and Microsoft recently released a paper discussing how they were able to perform a GPS spoofing attack that was able to divert drivers to a wrong destination (pdf) without being noticed. The hardware they used to perform the attack was low cost and made from off the shelf hardware. It consisted of a Raspberry Pi 3, HackRF SDR, small whip antenna and a mobile battery pack, together forming a total cost of only $225. The HackRF is a transmit capable SDR.
The idea is to use the HackRF to create a fake GPS signal that causes Google Maps running on an Android phone to believe that it's current location is different. They use a clever algorithm that ensures that the spoofed GPS location remains consistent with the actual physical road networks, to avoid the driver noticing that anything is wrong.
The attack is limited in that it relies on the driver paying attention only to the turn by turn directions, and not looking closely at the map, or having knowledge of the roads already. For example, spoofing to a nearby location on another road can make the GPS give the wrong 'left/right' audio direction. However, in their real world tests they were able to show that 95% of test subjects followed the spoofed navigation to an incorrect destination.
In past posts we've seen the HackRF and other transmit capable SDRs used to spoof GPS in other situations too. For example some players of the once popular Pokemon Go augmented reality game were cheating by using a HackRF to spoof GPS. Others have used GPS spoofing to bypass drone no-fly restrictions, and divert a superyacht. It is also believed that the Iranian government used GPS spoofing to safely divert and capture an American stealth drone back in 2011.
Other researchers are working on making GPS more robust. Aerospace Corp. are using a HackRF to try and fuse GPS together with other localization methods, such as by using localizing signals from radio towers and other satellites.
This would be great, my son could hunt for pokemon anywhere and I wouldn’t have to leave the house. 🙂
a
I remember the old move “The Net” with Sandra Bullock, where a group of cyberterrorists kills a guy by hacking the navigation system on his private plane to cause it to crash into a smokestack tower. Scary, one could actually do that for real now. I hope the DOD or USAF or whoever administers the GPS system now can develop a way for GPS users to guard against such an attack. Of course the best policy is never to rely 100% on GPS, good old paper maps don’t lie whereas GPS can.
Yeah yeah, I know, why the heck would anyone want to do that to someone anyway right? Well if some bad actor thinks there would be some benefit to doing it, you can bet sooner or later they will.
While it looks impressive in films, it authorsdo not check if their ideas match reality, meanin is it possible. Naviagtion equipment communicates via the same ARINC bus on board. Aircrafts use barometric altimeter and RA (Radar Altimeter for APP and landing) and not to my knowledge GNSS (Global Naviagtion Satellite Services Gallileo, Glonas and GPS) derived Altitude or FL. Further complicating things aircraft equipage and systems can differ for the same aircraft type, depending on the equipment that an airline ordered.
Aircraft either fly VFR (Visual Flight Rules) which means “visual”, or fly IFR (Instrument Flight Rules). IFR requires equippage with ILS, NDB, VOR and DME for naviagtion, wich are the primary terestrial ICAO navigation systems.
Since interfernce of GNSS is possible ICAO GNSS is not certified for sole means use for navigation, APP and landing. ICAO defined DME/DME as PRNAV backup in case of GNSS failure.
PS.: GNSS interference by military-jamming or civil use e.g. by privacy devices used in cars and trucks to jam GNSS tracking of vehicles. Privacy devices already produced problems in the past, when operated close to airports, first detected in JFK by FAA when I remeber correctly.
Spoofing is more problematic since the GNSS receiver cannot distinguish between real and spoofing signals. But since GNSS is not sole means for IFR, it is not possible since wrong positions by GNSS spoofing would raise an alarm in the FMS when the GNSS coordinates differ from the inertial naviagtion and VOR/DME and DME/DME derived position of an aircraft.
PS²: ICAO is currently working on standardizing multiconstallation GNSS receiver (using 2 or more systems e.g. Gallileo, Glonas and GPS). With multiconstallation GNSS receiver a spoofer would therefore also have to spoof the other systems used by multiconstallation receiver. To make things more diffuicult he would have to spoof not only 1575 MHz but also the other civil GNSS signals transmitted at between 1176 and 1215 MHz.
However the inertial navigation accumulates errors over time and has to be adjusted with GNSS which will result in a close loop allowing spoofers doing their job either way.
I have heard that the new Galileo signal cannot be spoofed, is it true ?
Why should Galileo be different to other GNSS(Global Naviagtion Satellite Services) signals like GPS. All GNSS systems signals are close to receiver noise, therefore spoofing is possible for all GNSS systems. However if you have multiconstallation GNSS receiver it would detect a discrapency between the the spoofed and the other GNSS systems used. A spoofer would therefore also have to spoof the other systems used by multiconstallation receiver.
PS.: I forgot to add, that to make things more difficult he would have to spoof not only 1575 MHz, but also the other civil GNSS signals transmitted at between 1176 and 1215 MHz.
Galileo is supposed to implement TESLA, so the packets are authentified by the receiver and it also prevents replay attacks.
That antenna looks totally not tuned to 1575.92MHz
The antenna looks to have a loading coil on it. Maybe spoofing lower Freq DGPS signals?
Still too small for those frequencies
Dis is sooo good …I can tink of spoofing armored car full of the socialistas monies!!!