HackRF and Portapack Featured in Recent Linus Tech Tips Video
Over on YouTube the Linus Tech Tips channel has recently released a video about the HackRF titled "It’s TOO Easy to Accidentally Do Illegal Stuff with This". Linus Tech Tips is an extremely popular computer technology YouTube channel. The HackRF is a popular transmit capable software defined radio that was released about 10 years ago. The portapack is an add-on for the HackRF that allows the HackRF to be used as a handheld device, and when combined with the Mayhem firmware, it enables easy access to some controversial tools that could get a user into a lot of legal trouble very fast.
In the video Linus, whose team is based in Canada, mentions that they decided to purchase the HackRF and similar devices because of the Canadian government's plan to ban various RF tools, including the Flipper Zero and HackRF.
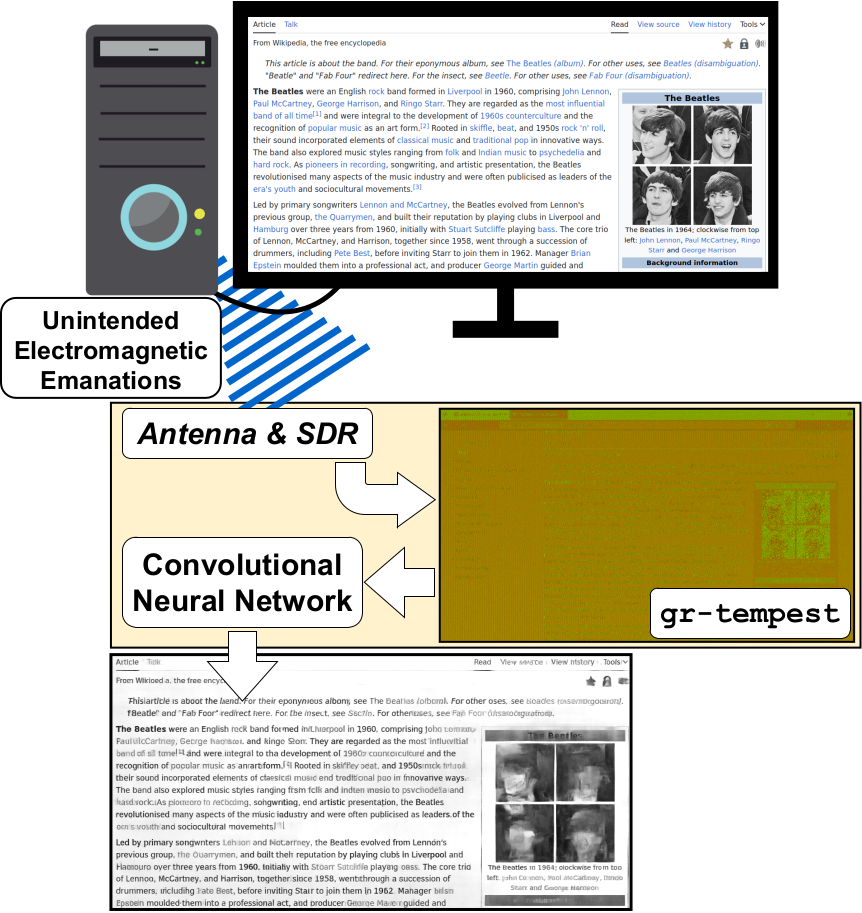
Linus then discusses and demonstrates "van eck phreaking" with TempestSDR, showing how he can use the HackRF to recover the video from a PC monitor wirelessly. He then goes on to demonstrate how the Portapack can be used to jam a wireless GoPro camera transmitting over WiFi.
Finally, Linus discusses the legality and morality of such devices being available on the market.