Reverse Engineering a Wireless Alarm with the HackRF
Wireless alarms consist of multiples devices such as sensors and detectors which all communicate to a central control box via RF signals. Blogger “fun over ip” decided that he wanted to understand the design and security measures used by his Verisure wireless alarm by reverse engineering the system.
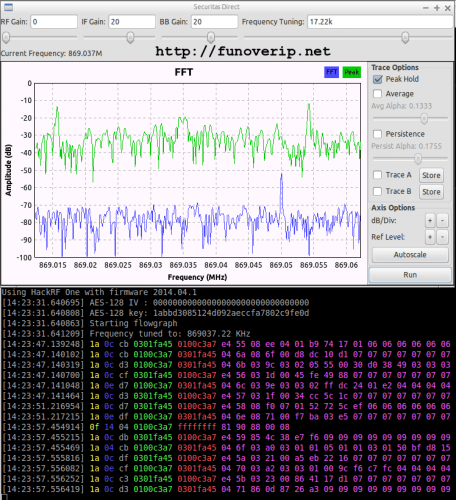
First, he took his HackRF software defined radio and monitored the 433 MHz and 868 MHz ISM bands whilst pushing keys on his alarms remote control. In the 868 MHz band he found a corresponding signal that had two spikes in the RF spectrum, indicating that it was likely a 2-FSK (frequency shift keyed) signal.
Next he created a GNU Radio program to demodulate the 2-FSK signal into a binary sequence. He then used Audacity to view and analyze the binary sequence, decoding it into 0’s and 1’s and determining the sync word (or access code). With further analysis he also determined the symbol rate and samples per symbol. With all this information gathered, he was then able to expand his GNU Radio program to automatically detect and decode packets sent by the various wireless devices connected to the alarm system.
His post goes into good detail about the steps that he took and is a great aide in understanding how to reverse engineer wireless protocols.