The Thought Emporium Explores IMSI Cell Phone Tracking and Other Advanced Cell Phone Attacks with Software Defined Radios
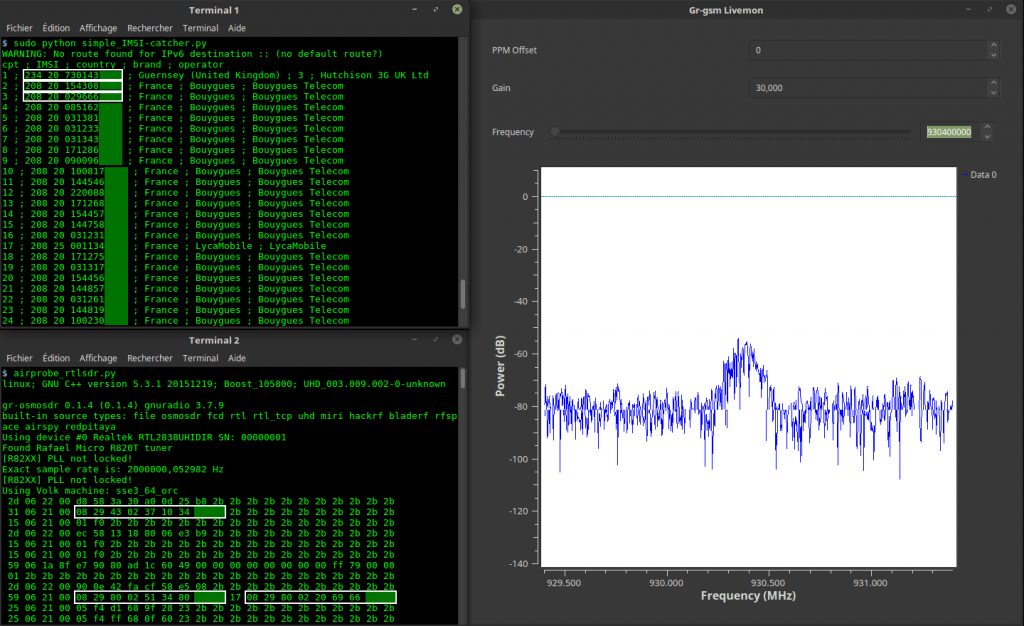
Over on YouTube, The Thought Emporium channel has uploaded a video outlining how mobile phones constantly leak unique IMSI identifiers over the air, making passive location tracking much easier than most people expect. While LTE and 5G improve security, older 2G and 3G protocols still expose permanent subscriber IDs that can be collected and linked to movement over time.
The video highlights how accessible this surveillance is. A cheap RTL-SDR USB dongle, basic antenna, and free software pre-installed on DragonOS are enough to passively collect IMSI numbers from nearby phones running on 3G. Once you know a person's unique IMSI number, you can easily track their movements if you have cheap radios monitoring the areas they frequent.
They also show how it's possible to use a more advanced TX-capable SDR like a USRP B210 to create a Stingray device, which is a fake cell-tower base station that you can force nearby cell phones to connect to. Once connected to the Stingray, all communications from your phone can be tapped. Finally, they discuss SS7 attacks, which, while difficult and/or expensive to gain access to the SS7 walled garden, can allow malicious actors to easily reroute security-related messages, such as 2-factor authentication.
The video finishes with potential defenses, including turning phones off when needed, forcing more secure LTE/5G-only connections, and using tools that detect fake cell towers. Privacy-focused mobile services that rotate identifiers are also discussed.