SigintOS Version 2.0 Community Edition Released
SigintOS is an Ubuntu based distribution with a number of built in signal intelligence applications for software defined radios such as the RTL-SDR and TX capable SDRs like the HackRF, bladeRF and USRP radios.
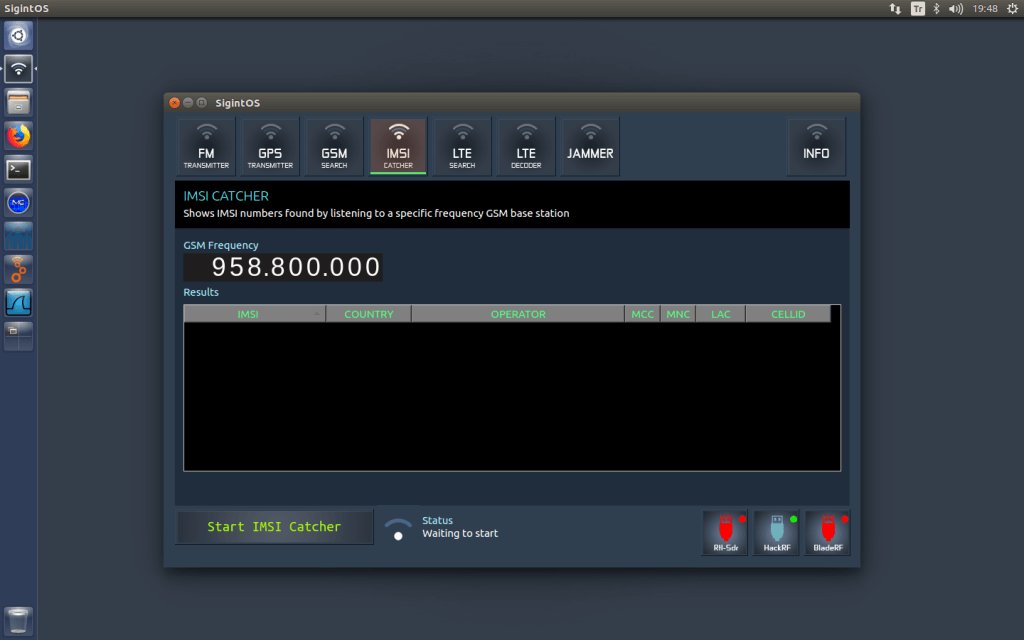
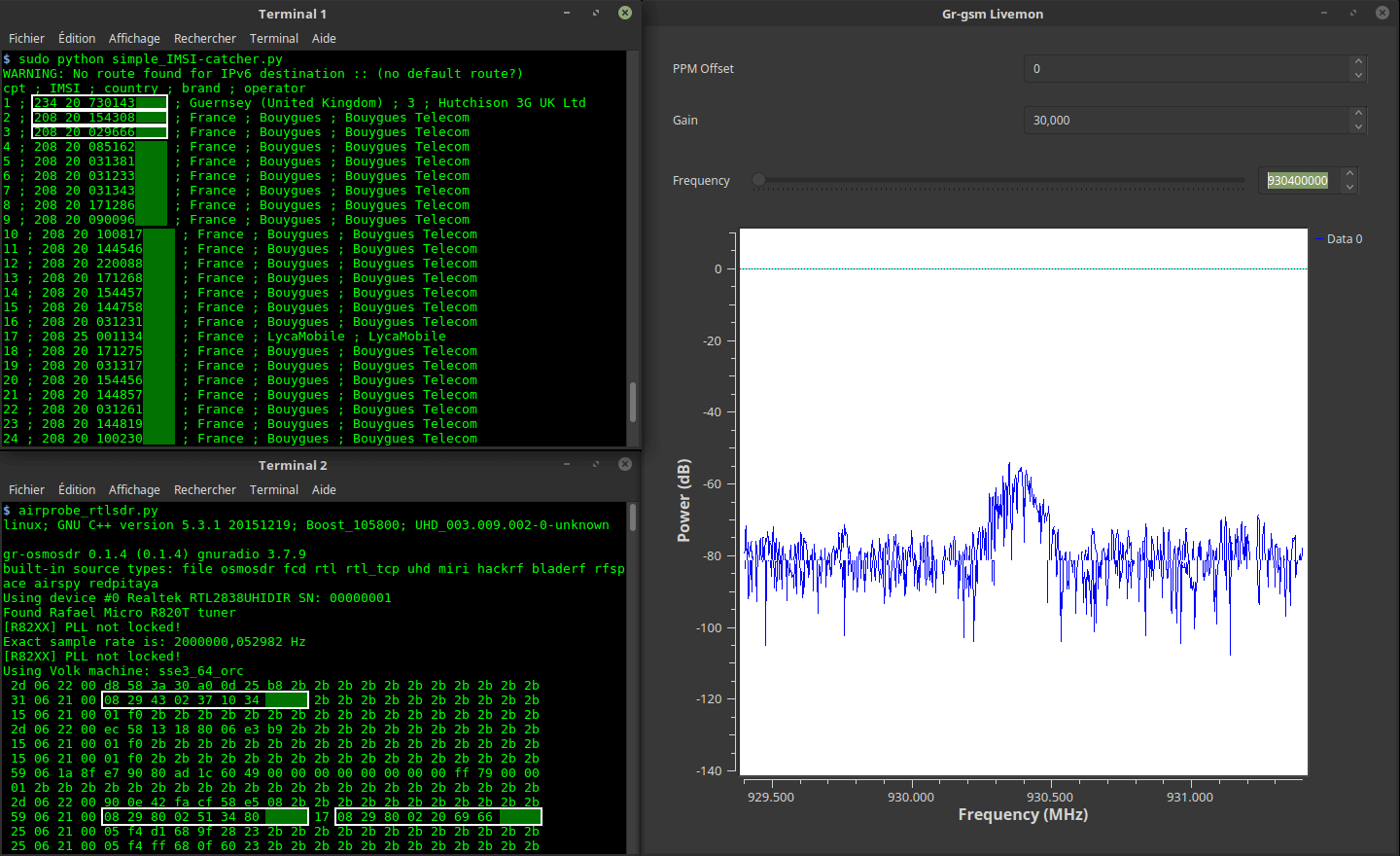
The OS has a built in launcher UI that helps to automatically launch and set up parameters for various programs and GNU Radio scripts that are commonly used. Examples include an FM transmitter, GPS transmitter, GSM base station searcher, IMSI catcher, LTE base station searcher, LTE decoder and a jammer.
Recently the team behind SigintOS have released version 2.0 Community Edition. The team write on their release page:
About Community Edition
SigintOS 2.0 Community Edition; It was developed to provide a much better experience to its users. With a new interface, more stable and powerful infrastructure and development environment, it allows users to develop new tools in addition to existing tools.
Developing Signal Intelligence tools is now much easier with SigintOS™
It is now much easier to develop your own tools with SigintOS™, which contains the world’s most famous and free signal processing and communication software. You can develop them effortlessly with tools such as QT and KDevelop.
Say hello to the 5G World!
SigintOS™ offers you all the possibilities of the 5G world, free of charge and effortlessly!
Whats News?
- A completely new look.
- A more stable and robust infrastructure.
- Latest drivers and software.
- User-friendly interface that prioritizes habits.
SOFTWARE LIST
Most used software and features
- Open5GS
- srsRAN 4G
- YateBTS
- Gqrx
- GnuRadio 3.8
- SigDigger
- SDRAngel
- ADSB Viewer
- Dump1090
- OpenCPN
- GPredict
- BladeRF
- HackRF
- Rtl-SDR
- USRP – UHD Drivers
- Kalibrate RTL & HackRF
- All Gr Modules
- SigintOS SDR Hardware Monitor Widget
- QTCreator
- KDevelop
- Mysql
- MongoDB
- Apache Web Server
- Php
- And more …