Using a Software Defined Radio to Send Fake Presidential Alerts over LTE
Modern cell phones in the USA are all required to support the Wireless Emergency Alert (WEA) program, which allows citizens to receive urgent messages like AMBER (child abduction) alerts, severe weather warnings and Presidential Alerts.
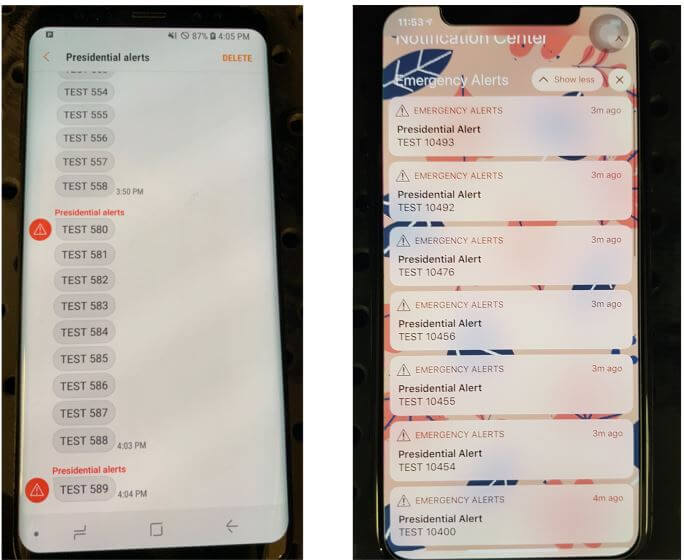
In January 2018 an incoming missile alert was accidentally issued to residents in Hawaii, resulting in panic and disruption. More recently an unblockable Presidential Alert test message was sent to all US phones. These events have prompted researchers at the University of Colorado Boulder to investigate concerns over how this alert system could be hacked, potentially allowing bad actors to cause mass panic on demand (SciHub Paper).
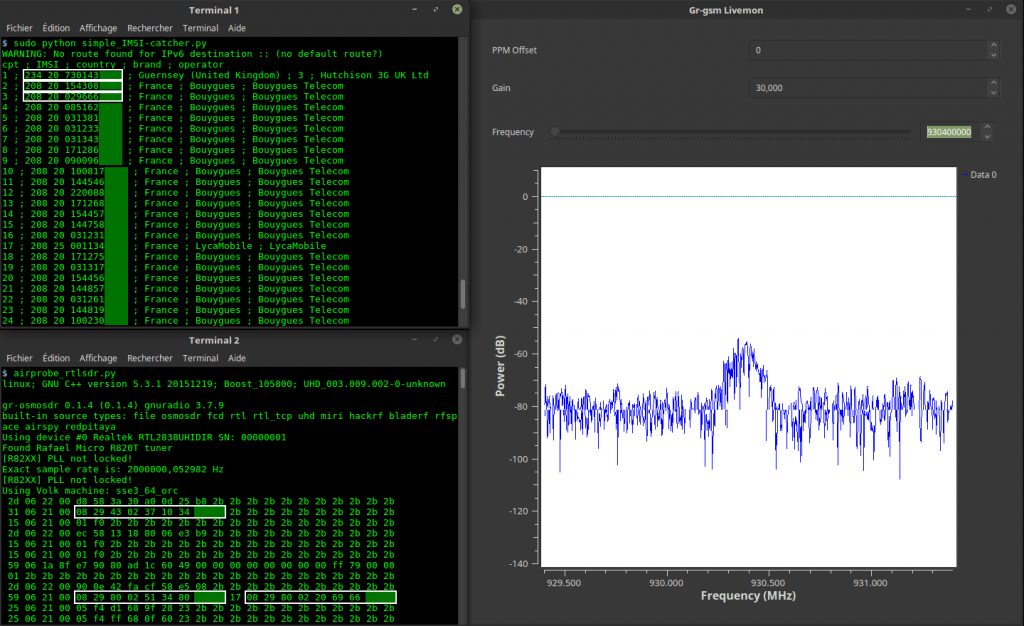
Their research showed that four low cost USRP or bladeRF TX capable software defined radios (SDR) with 1 watt output power each, combined with open source LTE base station software could be used to send a fake Presidential Alert to a stadium of 50,000 people (note that this was only simulated - real world tests were performed responsibly in a controlled environment). The attack works by creating a fake and malicious LTE cell tower on the SDR that nearby cell phones connect to. Once connected an alert can easily be crafted and sent to all connected phones. There is no way to verify that an alert is legitimate.