Eavesdropping on Sensitive Data via Unencrypted Geostationary Satellites
Recently, Wired.com released an article based on research by researchers at UC San Diego and the University of Maryland, highlighting how much sensitive unencrypted data many geostationary satellites are broadcasting in the clear.
The researchers used a simple off-the-shelf 100cm Ku-band satellite dish and a TBS-5927 DVB-S/S2 USB Tuner Card as the core hardware, noting that the total hardware cost was about $800.
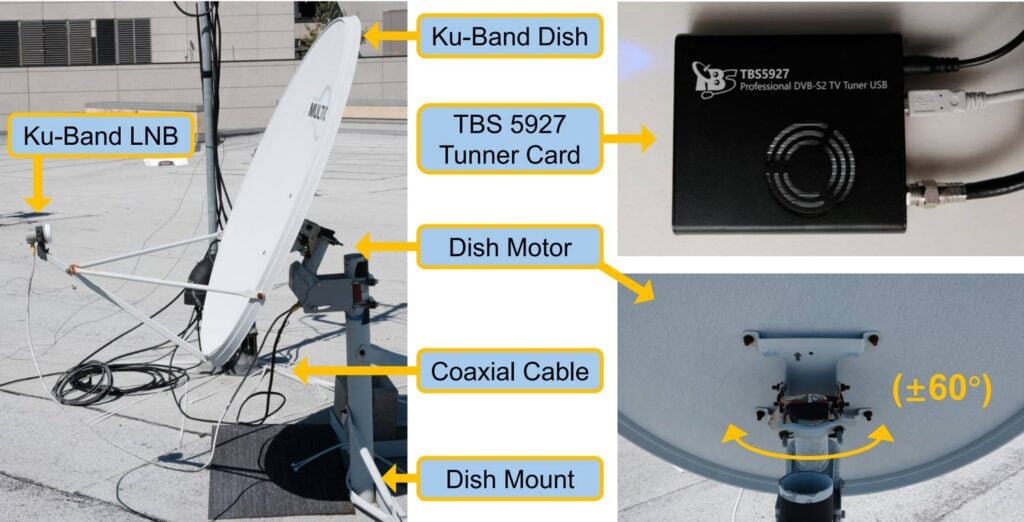
After receiving data from various satellites, they found that a lot of the data being sent was unencrypted, and they were able to obtain sensitive data such as plaintext SMS and voice call contents from T-Mobile cellular backhaul and user internet traffic. The researchers notified T-Mobile about the vulnerability, and to their credit, turned on encryption quickly.
They were similarly able to observe uncrypted data from various other companies and organizations, too, including the US Military, the Mexican Government and Military, Walmart-Mexico, a Mexican financial institution, a Mexican bank, a Mexican electricity utility, other utilities, maritime vessels, and offshore oil and gas platforms. They were also able to snoop on users' in-flight WiFi data.
Cellular Backhaul
We observed unencrypted cellular backhaul data sent from the core network of multiple telecom providers and destined for specific cell towers in remote areas. This traffic included unencrypted calls, SMS, end user Internet traffic, hardware IDs (e.g. IMSI), and cellular communication encryption keys.Military and Government
We observed unencrypted VoIP and internet traffic and encrypted internal communications from ships, unencrypted traffic for military systems with detailed tracking data for coastal vessel surveillance, and operations of a police force.In‑flight Wi‑Fi
We observed unprotected passenger Internet traffic destined for in-flight Wi-Fi users on airplanes. Visible traffic included passenger web browsing (DNS lookups and HTTPS traffic), encrypted pilot flight‑information systems, and in‑flight entertainment.VoIP
Multiple VoIP providers were using unencrypted satellite backhaul, exposing unencrypted call audio and metadata from end users.Internal Commercial Networks
Retail, financial, and banking companies all used unencrypted satellite communications for their internal networks. We observed unencrypted login credentials, corporate emails, inventory records, and ATM networking information.Critical Infrastructure
Power utility companies and oil and gas pipelines used GEO satellite links to support remotely operated SCADA infrastructure and power grid repair tickets.
The technical paper goes in depth into how they set up their hardware, what services and organizations they were able to eavesdrop on, and how they decoded the signals. The team notes that they have notified affected parties, and most have now implemented encryption. However, it seems that several services are still broadcasting in the clear.
Wish I didn’t take down all my FTA Ku-band satellite dishes. This sounds interesting. Thanks for posting.