Recently wired.com ran a story that explains how research hackers from KU Leuven university in Belgium have been able to clone a Tesla car key fob within seconds. With the cloned keyfob they are then able to open the Tesla's door, start the motors and drive away. The researchers believe this attack could also work on cars sold by McLaren and Karma, as well as Triumph motorcycles.
Like most automotive keyless entry systems, Tesla Model S key fobs send an encrypted code, based on a secret cryptographic key, to a car's radios to trigger it to unlock and disable its immobilizer, allowing the car's engine to start. After nine months of on-and-off reverse engineering work, the KU Leuven team discovered in the summer of 2017 that the Tesla Model S keyless entry system, built by a manufacturer called Pektron, used only a weak 40-bit cipher to encrypt those key fob codes.
The researchers found that once they gained two codes from any given key fob, they could simply try every possible cryptographic key until they found the one that unlocked the car. They then computed all the possible keys for any combination of code pairs to create a massive, 6-terabyte table of pre-computed keys. With that table and those two codes, the hackers say they can look up the correct cryptographic key to spoof any key fob in just 1.6 seconds.
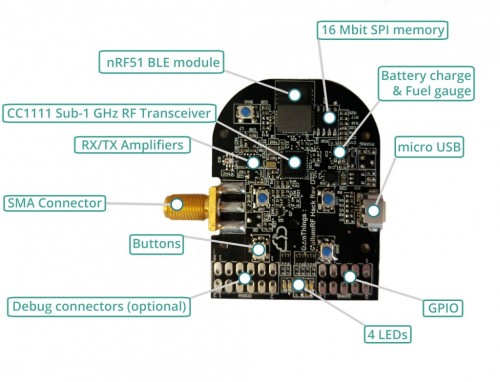
The attack hardware consists of a Yardstick One dongle, a Proxmark RFID/NFC radio, and a Raspberry Pi connected to the 6TB hard drive containing the database of pre-computed keys. All together the cost of such a system is under $600.
The actual attack works by first bringing the RFID antenna and radio near the car and recording vehicles identifier code which is periodically transmitted by the car. Then the antenna is brought near to the owners keyfob and impersonates the car using the identifier code. This tricks the keyfob into sending out encrypted response codes which are then decrypted by the 6TB lookup table on the hard drive. The Yardstick One is then used to transmit the final unlock code at 433.92 MHz.
Tesla have since responded by noting that cars sold after June 2018 have improved encryption and aren't vulnerable to this attack, and that owners of cars manufactured earlier are able to enable an option that requires a PIN code to be entered. Owners could also take extra precautions such as using an RFID blocking pouch. Tesla vehicles also have built in GPS tracking which may deter thieves.
The video below shows the attack in action, and a short overview paper by the researchers can be found here.