Tutorial on Performing a Replay Attack with a HackRF and Universal Radio Hacker
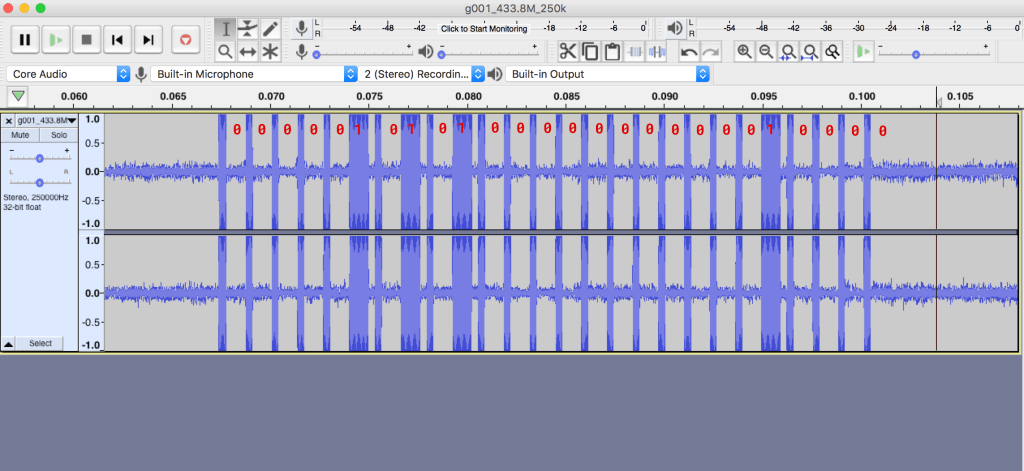
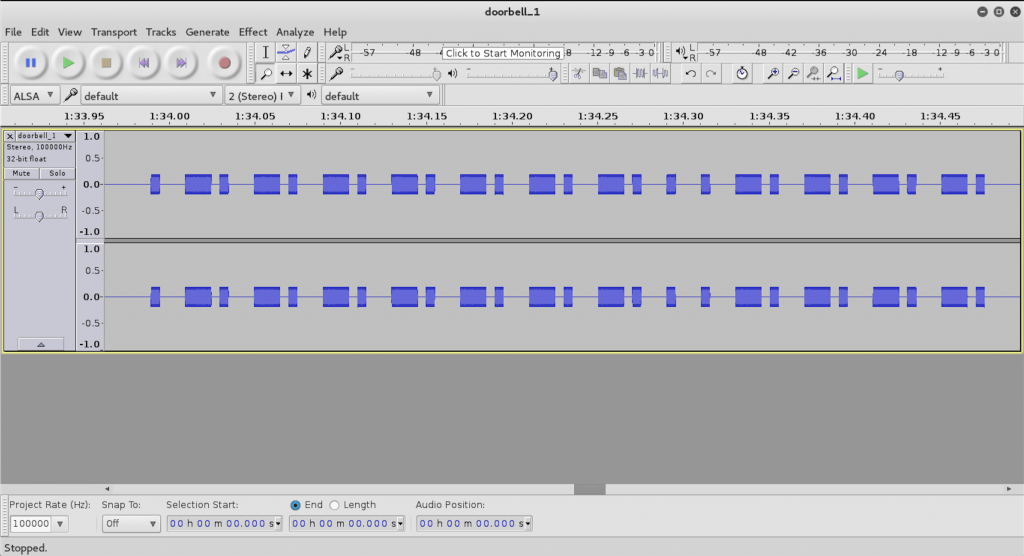
Over on YouTube channel Tech Minds has uploaded a short tutorial video that shows how to perform a replay attack with a HackRF and the Universal Radio Hacker software. A replay attack is when you record a control signal from a keyfob or other transmitter, and replay that signal using your recording and a TX capable radio. This allows you to take control of a wireless device without the original keyfob/transmitter. This is easy to do with simple wireless devices like doorbells, but not so easy with any system with rolling codes or more advanced security like most car key fobs.
In the video Tech Minds uses the Universal Radio Hacker software to record a signal from a wireless doorbell, save the recording, replay it with the HackRF, and also analyze it.