Help Support RadioCapture – A Project that Records Entire Trunked Radio Systems and Provides Online Access to Audio
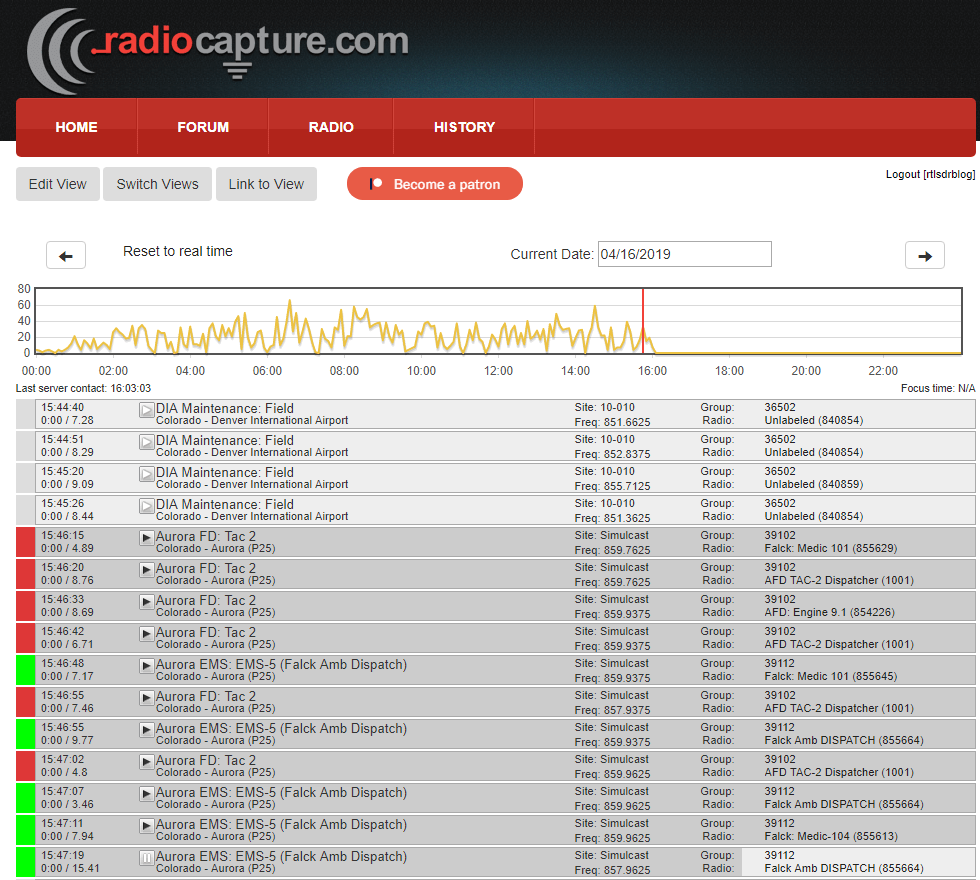
RadioCapture.com is a website run by Matt Mills that is capable of automatically capturing trunked radio communications from various agencies such as the emergency services and creating publicly accessible historical and live logs of the audio. This is a concept different to radio scanner streams, as all audio is logged and historical audio can be accessed easily at any time.
The system is based on SDR hardware such as the RTL-SDR. Currently Matt runs a receiver in Denver and captures Denver PD which can be listened to on the site without needing to log in. Once logged in (registration is free), other talkgroups available include various agencies in Colorado, New Jersey and Pennsylvania.
Recently Matt has put a call out for people to help support the site via Patreon. He notes that RadioCapture is currently run as a hobby, but with monetary support he hopes to be able to expand the site into a business and have receivers listening and uploading worldwide. He writes:
Hey! Thanks for supporting the continued operation and development of Radiocapture.com. This is a hobby project I've been working on this since late 2011. I'd like to turn it into a real business with your help.
Radiocapture.com is a software defined radio system I built that captures entire trunked radio systems. It demodulates and captures every call on every channel of one, or many systems.
A single RadioCapture server can capture hundreds of simultaneous voice transmissions and a bunch of sites, additionally it's designed in such a way that it can run across multiple computers. My biggest RF site uses 3 machines to capture 19 P25 systems, and easily hits more than 100 active voice channels recordings simultaneously every day.
Matt has also noted that if the site is able to become self-sustaining via Patreon, he hopes to also be able to bring out a RadioCapture kit consisting of 10-16 RTL-SDR dongles, hubs and cables which would allow anyone to easily capture and upload almost all trunked communications from their area. He also notes that at the time of writing:
RadioCapture has 701790271 unique recordings of 503779875 unique transmissions (some calls get captured on multiple transmitters) from the 21 systems that have been captured
If you're interested in talking to Matt about the site, you can also join his Rocket.Chat room at radiocapture.chat.