Snooping Network Traffic from LAN Cables with an RTL-SDR or HackRF
Mordechai Guri is a cyber-security security researcher at Israel's Ben Gurion University of the Negev. Recently Guri has described a method for sniffing network data from LAN Ethernet cables over an air gap through the use of RTL-SDR or HackRF software defined radios. Guri's paper is available directly here.
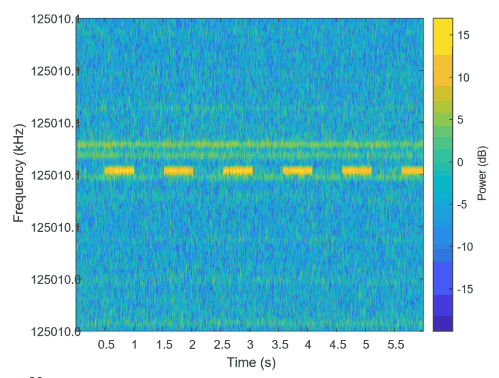
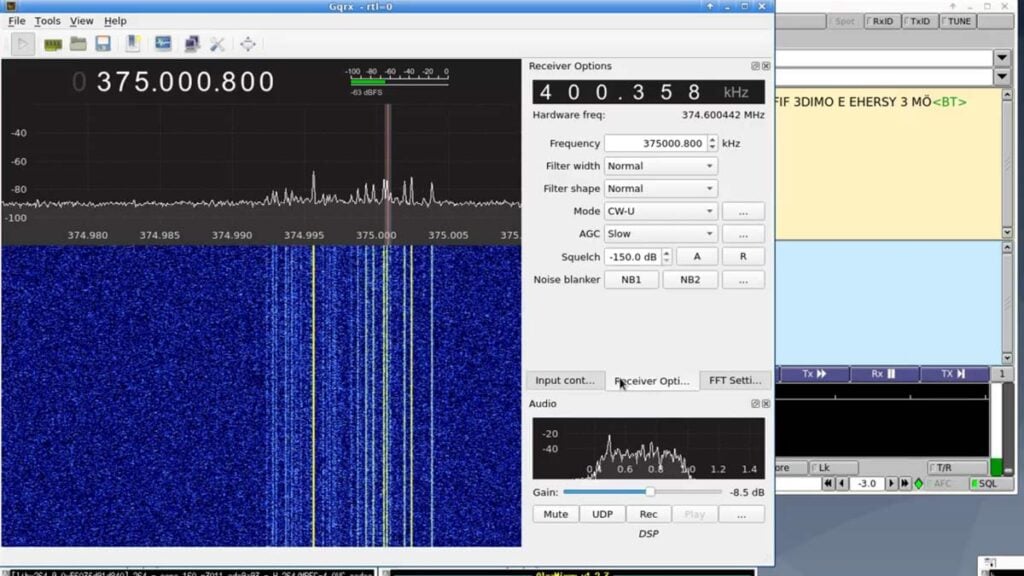
The idea behind the attack is that ethernet cables can act as an antenna, leaking signals at frequencies which can easily be sniffed by a SDR. The specific technique in the paper does not decode normal network traffic, instead it requires that malicious code which modulates a custom signal over the ethernet cable be installed on the PC first. The technique used appears to be similar to what the Etherify software by SQ5BPF uses, which modulates data in morse code by turning the network card on and off.