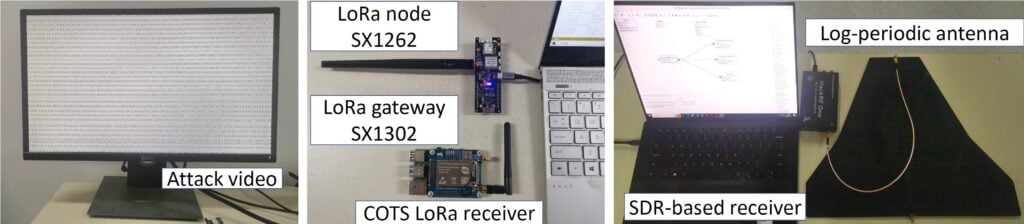
TEMPEST-LoRa: Emitting LoRa Packets from VGA or HDMI Cables
University researchers from China have recently shown in a research paper that it is possible to maliciously cause a VGA or HDMI cable to emit LoRa compatible packets by simply displaying a full-screen image or video. This has potential security implications as a malicious program could be used to leak sensitive information over the air, completely bypassing any internet or air-gap security systems.
In the past, we have demonstrated that TEMPEST techniques can be used to spy on monitors and security cameras by analyzing the unintentional signals they emit. This research takes the idea a step further by determining what particular images need to be displayed to create a LoRa packet with data.
In the paper, the researchers mention using either off-the-shelf LoRa devices or low-cost SDRs such as the HackRF to receive the packets. The advantage of the SDR method is that it allows for customization of the frequency and the use of LoRa-like packets, which can achieve even longer ranges and higher data rates. The team show that they were able to achieve a receive range of up to 132 meters and up to 180 kbps of data rate.