Over on YouTube Rob VK8FOES has been uploading some fairly comprehensive demonstrations and tutorials showing how to crack a GSM capture file which can be recorded with any SDR.
It's well known now that GSM aka 2G communications are insecure, with the encryption having been breakable on a standard PC for a long time now. It is for this reason that GSM is now mostly phased out, however in many regions the GSM system is still operational in reduced capacity due to some legacy users who are mostly industrial.
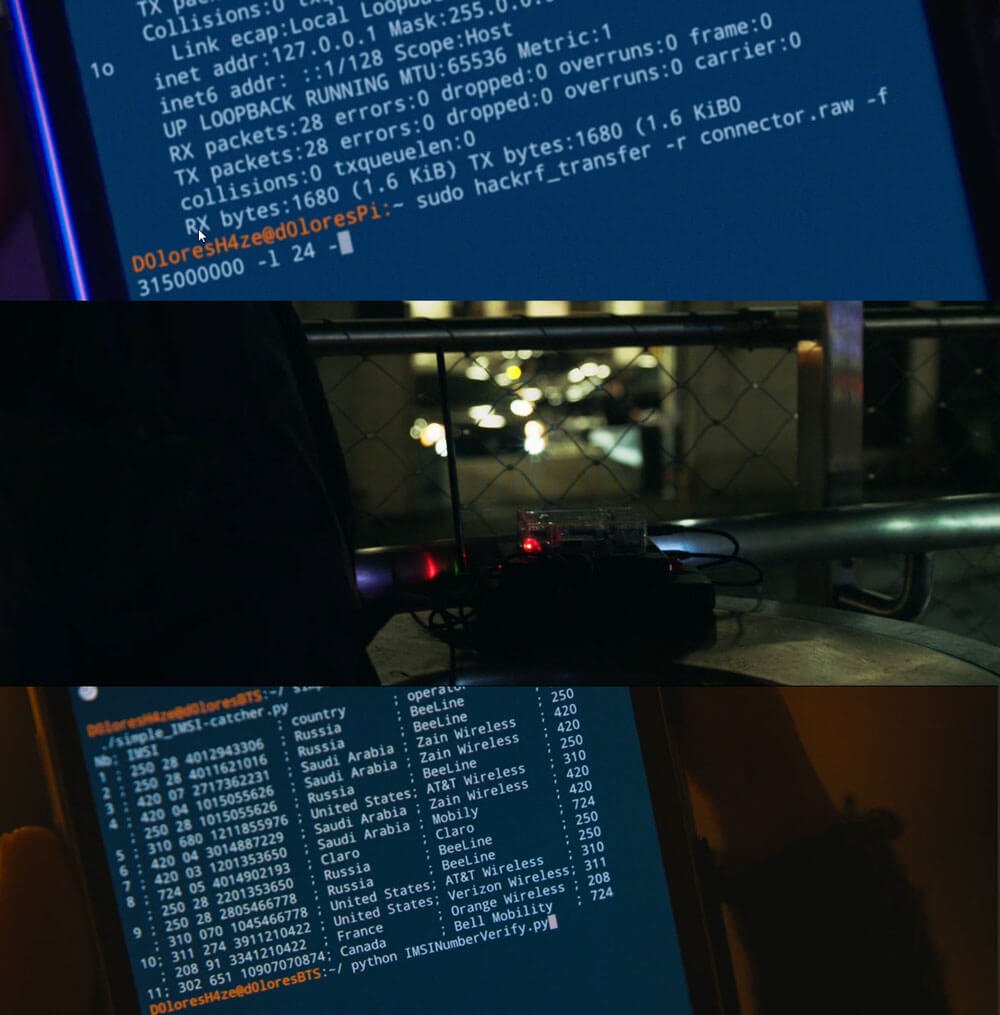
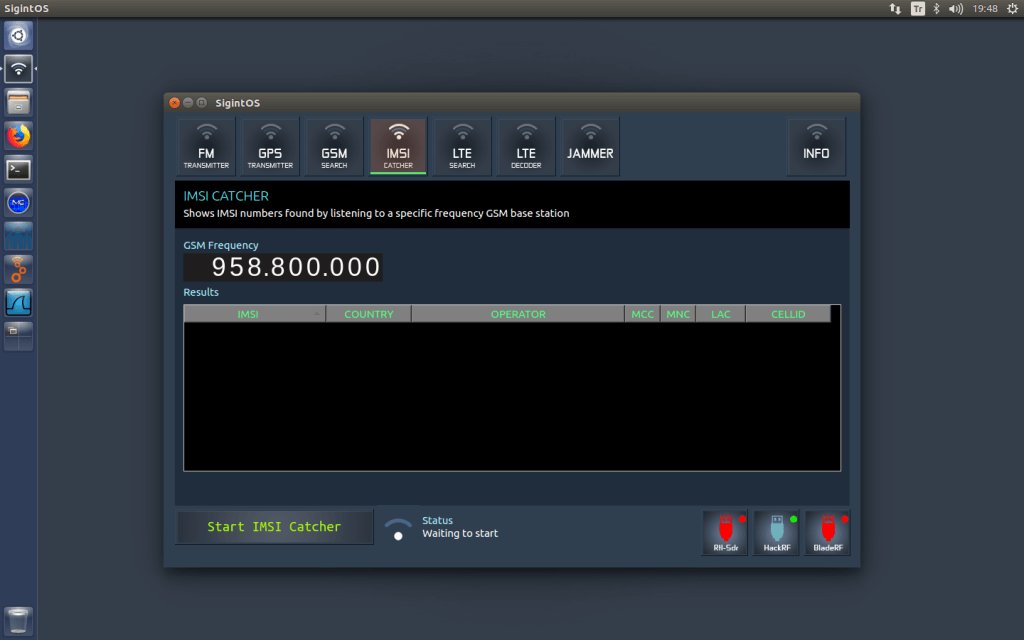
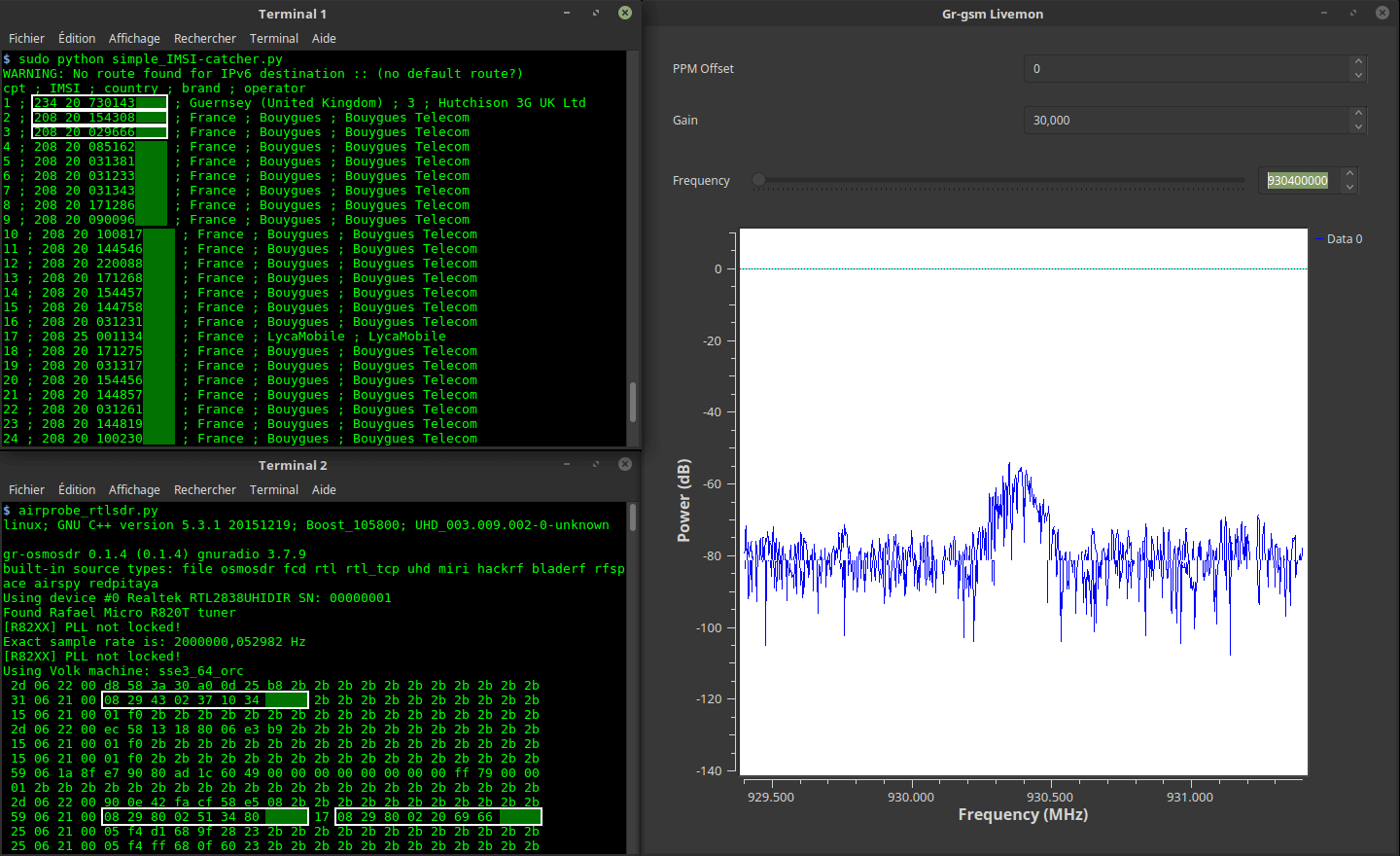
In his video Rob makes use of the opensource Airpobe GSM decoder tool, as well as the opensource Kraken tool (not to be confused with KrakenSDR) which is a brute force password cracking tool.
We want to note that doing this is only legal if it is your own communication that has been recorded, or you have permission from the communicating parties.
My GSM cracking content has been getting quite a lot of attention lately. Previous videos of mine relating to this topic were only boring screen recordings with no real explanation on what steps are required to crack the A5/1 stream cipher and decrypt GSM traffic by obtaining the Kc value.
I was bored one day and decided to present a live-style workflow of how hackers and security researchers 'crack' 2G cellular communications in real-time. Be warned that if you don't have an interest in cryptography or cellular network security, you might find this video rather boring.
The GSM capture file used in this video, to my knowledge, has never been publicly cracked before. 'capture_941.8M_112.cfile' was recorded and uploaded with permission by the owner of the data themselves as a decoding example for testing Airprobe.
I make a few mistakes in the video that I can't be bothered editing out. But they are not critical, just myself misreading a number at the 10 minute mark somewhere, and saying the wrong name of a software tool at 17 minutes.
Additionally, l am not a GSM technology engineer, nor a cryptography expert. I do my best to explain these concepts in a simple and easy to understand way. But due to my limited knowledge of these subjects, it's possible that some of this information may be incorrect or lacking context.
However, this video will still allow you to crack a real GSM capture file if you are able to follow along with my flip-flopping style of presentation. Haha. But please, only replicate this tutorial on GSM data that originated from YOUR OWN mobile phone. Do not attempt to decrypt private telecommunications from any other cellular subscriber, EVER.