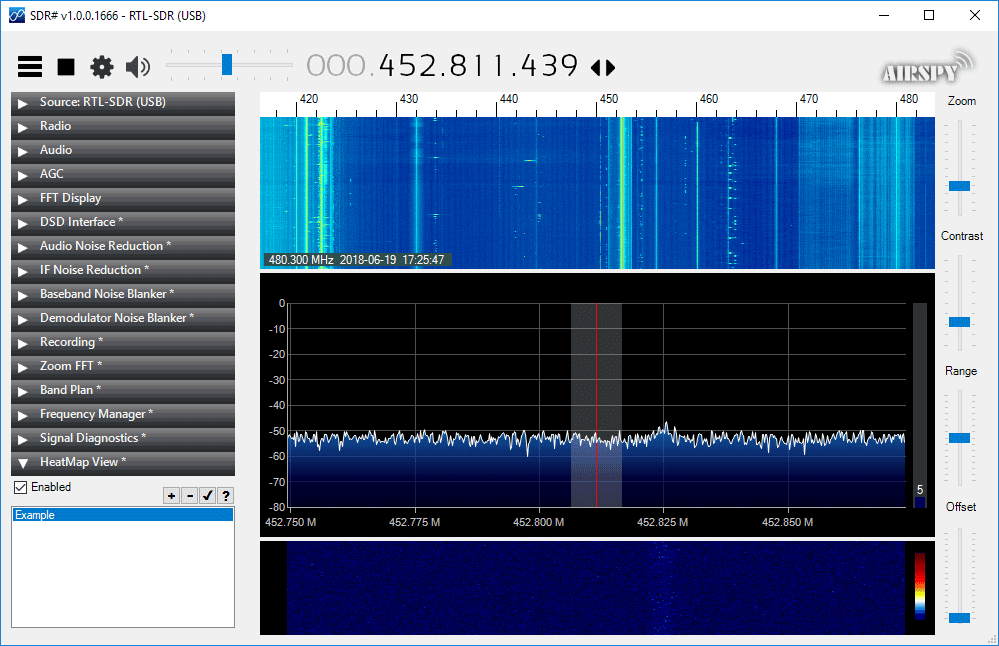
New TETRA Trunk Tracker for use with SDR# and the TETRA Demodulator Plugin
Over on our forums user thewraith2008 has just released news about his new software called TETRA Trunk Tracker. The software works in conjunction with the TETRA demodulator plugin for SDR#. It works by using two dongles, one to monitor a TETRA trunking channel, and the other to decode voice audio, although a single receiver mode is also available which works with a reduced and fixed bandwidth.
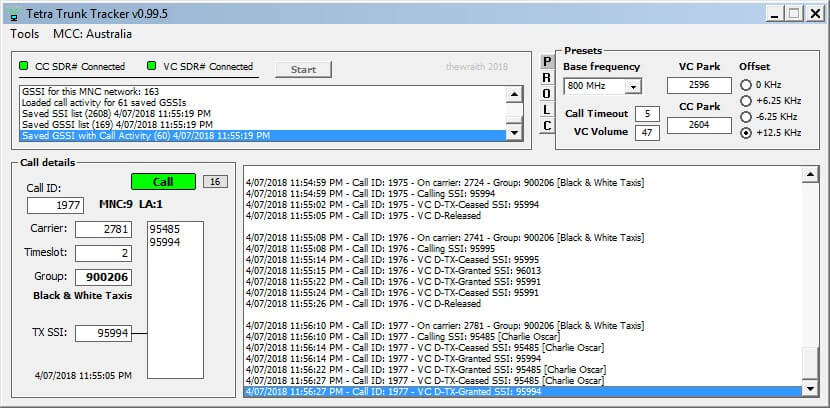
The post reads:
TETRA Trunk Tracker will follow calls on a TETRA network.
TETRA Trunk Tracker reads DATA that is output from the SDR# plug-in TETRA Demodulator (by TSSDR) via the 'Network Info' calls log window.
It interprets this DATA to determine when a call is set-up, then instructs SDR# (VC) to move to the carrier (frequency) that the call will be on.
It will also watch out for other PDUs to determine when a SSI starts or completes transmissions and when calls are complete (Released).
Features:
- A basic call recording (All or Selective call recording).
- Display current call details with list of seen SSIs for that call. (SSI populate as they TX).
- GSSI holding - will only allow calls with selected GSSI to be heard.
- Call lockout based on GSSI. Can be unchecked in list to lockout GSSI.
- Call Priority. (Only normal version)
- GSSI weighted 0-9, 9 is highest. If on active call and other call event occurs, if new call has higher
- priority then will switch to it.
- Collect/Save all seen GSSIs with Labels and Priority, By Network.
- Collect/Save seen SSIs with Labels and Last seen Date/Time, By Network.
- Set a call time-out. Returns to idle state if call does not see a release PDU
after X time in seconds.- Log call events to screen and file, if enabled.
- Log raw CC and VC PDU messages as seen by the 'TETRA Demodulator' plug-in, if enabled.
- Log GSSI daily call activity. (Simple version does not play calls when this is selected)
- Set base frequency via UI.
- Set CC park carrier # via UI.
- Set VC park carrier # via UI.
- Suppress some PDUs. (unchecked is mainly for testing only)
- Suppress lockout messages.
- Sort SSI and GSSIs/Lockouts (by GSSI). This only occurs on start-up.
- Country Code label, defined via file (shown as menu item)
- Network label, defined via file (shown in tool tip where MNC,LA is in 'Call Details' panel)
- Location Area label, defined via file (shown in tool tip where MNC,LA is in 'Call Details' panel)
Only shown when Network label used.- Ignores Encrypted PDUs (with no reference to them)
- Set a seen GSSI priority via UI.
- Update a seen GSSI/SSI label via UI.
- Call active indicator.
- Restore SDR# windows to a defined position.
If the TETRA Demodulator does not work for you this program will do nothing to change that.
This is the third release of this program. (TETRA Trunk Tracker v0.99.6)
And 2nd release for (TETRA Trunk Tracker v0.99.6s - Simple)
Two versions are available:
- Normal (Uses 2 SDR# and 2 Dongles) with TETRA Demodulator and Net Remote plug-ins
- Simple (Uses 1 SDR# and 1 Dongles with some features not available) with TETRA Demodulator and Net Remote plug-ins
Backup your "Tetra-trunk-tracker.dat" settings file.
Then delete "Tetra-trunk-tracker.dat" as it has changed and old one will cause error on load.
Some work as gone into trying to make TETRA Trunk Tracker easier to run once the initial setup has been done.
A MCC (Country Code) label file is included for your convenience "TETRA_mcc.txt".
It has only been tested on Windows 7 - Professional SP1 (32 bit), English
You MUST have a PC that is capable of running SDR# x 2 with the TETRA plug-in. (Not overloaded CPU usage.)
It is in alpha stage. This means is may contain errors that may cause issues with the other programs it
works with. i.e. crashing them or itself.
The TETRA plug-in currently been developed by TSSDR is also in early development. Because of this
any changes made in plug-in releases most likely will break this program.
I have created it to suit my needs. And it currently works for me with the TETRA network I monitor.
I make no claim that it will work for other networks.
Please read the provided files for set-up and usage:
- TTT_set-up_manual.pdf
- TTT_Features_and_Usage.pdf
I have tried to be as thorough as possible with the documentation to explain usage and features.
I believe any questions can be answered by reading these files.
These files most likely are not complete and contain errors and are not laid out as good as they could be.
It only works with the provided TETRA plug-in supplied in zip. (2018-June-06).
This version uses a custom compiled version of 'Net Remote' supplied in zip
It is only meant to be a temporary solution until something better comes along.
Hopefully all goes well for you setting it up.
Download link
MD5 HASH 6f33fcf9662573b77e177e899793b9f9
Video showing starting it and it running
Video showing starting it and it running - Simple version