RS41 RadioSonde Tracking Software
A radiosonde is a small weather sensor package that is typically attached to a weather balloon. As it rises into the atmosphere it measures parameters such as temperature, humidity, pressure, GPS location etc, and transmits this data back down to a receiver base station using a radio signal. The RS41 is one of the newer radiosonde modules sold by radiosonde manufacturer Vaisala, and is currently one of the most popular radiosondes in use by meteorological agencies. The signal is typically found at around 400 MHz and can be received with an RTL-SDR and an antenna tuned for 400 MHz. We have a general tutorial on radiosonde decoding available here.
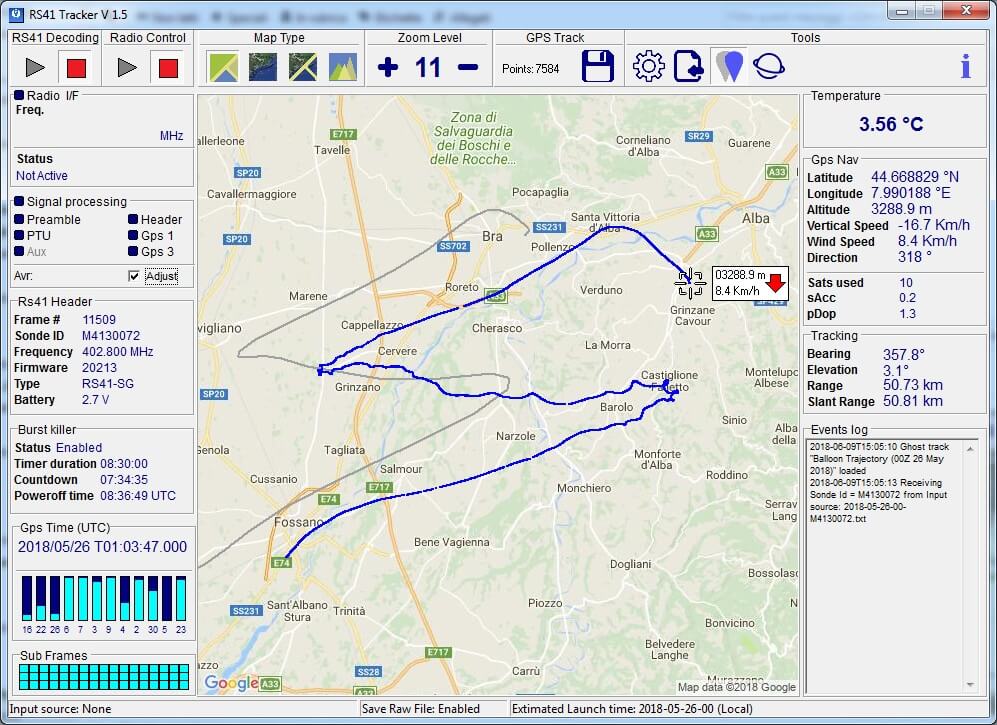
There are several software packages that can decode RS41 data, such as the multi-radiosonde decoder Windows program called SondeMonitor (25 euros), or the free Linux command line software called RS. Recently a new free Windows GUI based RS41 decoder has been released by IW1GIS. The software can display on Google maps the current location and previous path of the radiosonde, as well as it's weather data telemetry.
Main features are:
- Directly decoding of GFSK signal received by the FM radio receiver (the use of a Software Defined Radio is recommended).
- Capability to connect and command SDRSharp software by mean of Net Remote Control plugin.
- Advanced frequencies scan and decode: RS41 Tracker is able to look for RS41 radiosonde signal in a given list of frequencies, starting the radiosonde decoding when a valid signal is detected.
- Real time showing radiosonde position on google map (internet connection is required)
- Map auto centered on radiosonde position
- Map type selectable by user (road, satellite, hybrid, terrain).
- Burst killer detailed information and launch time estimation.
- Radiosonde RAW data save
- Post processing of RS41 RAW data file
- Tracking information (elevation, bearing, slant range)
- Radiosonde track saved on kml file
- Ghost track shown on map (loading from kml file)
- Shortcut for google maps in browser