Developing an Alternative To GPS with a HackRF
The LA Times recently ran a story that discussed how vulnerable GPS is to malicious spoofing. This has been well known for a number of years now with researchers having been successful at diverting a 80-million dollar yacht off it's intended course 5 years ago. We've also seen GPS spoofing performed with low cost TX capable SDRs like the HackRF. For example we've seen researchers use GPS spoofing to cheat at "Pokemon Go" an augmented reality smartphone game and to bypass drone no-fly restrictions.
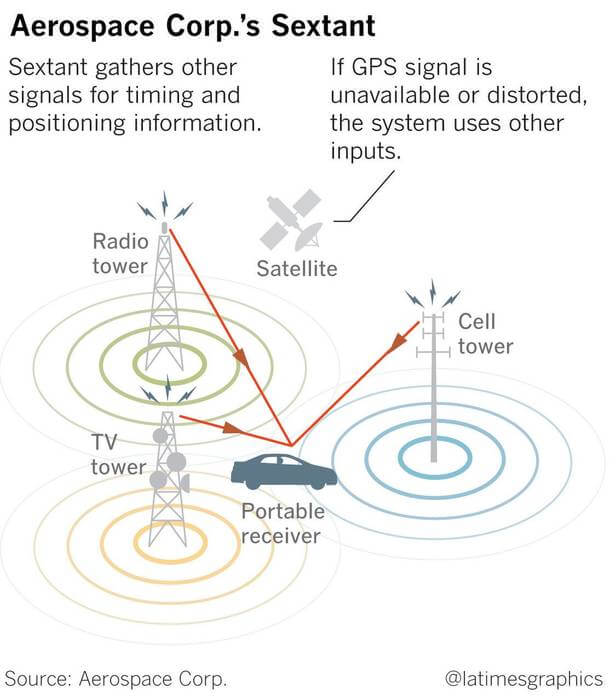
The article in the LA times also discusses how a group of researchers at Aerospace Corp. are testing GPS alternatives and/or augmentations, that improve resilience against spoofing. The system being developed is called 'Sextant', and it's basic idea is to use other sources of information to help in determining a location.
Other sources of information include signals sources like radio, TV and cell tower signals. It also includes taking data from other localization signals like LORAN (a long range HF based hyperbolic navigation system), and GPS augmentation satellites such as the Japanese QZSS which is a system used to improve GPS operation in areas with dense tall buildings, such as in many of Japans cities. More advanced Sextant algorithms will possibly also incorporate accelerometer/inertial data, and even a visual sensor that uses scenery to determine location.
Most likely a key component of Sextant will be the use of a software defined radio and from the photos in the article the team appear to be testing Sextant with a simple HackRF SDR. While we're unsure of the commercial/military nature of the software, and although probably unlikely, hopefully in the future we'll see some open source software released which will allow anyone to test Sextants localization features with a HackRF or similar SDR.